It is impossible to allow communication between computer systems, servers, routers, switches, and other network-enabled devices without following a set of protocols. Without protocols, devices would be unable to understand the electronic signals sent between them via network connections. Every day, billions of individuals utilize network protocols, whether they are aware of it or not. Each time you connect to the internet or make a phone call, you are using network protocols. While you may not be familiar with how network protocols function or how often you come across them, they are required for any use of the internet or digital communications.
Related article: What is Network Performance Monitoring?
Let’s dive deep into the concepts of network protocol, how it works, as well as a list of network protocols.
What is Network Protocol?
Network protocols are a set of rules, conventions, and data structures that describe how devices exchange data over networks. In other words, network protocols can be compared to languages that two devices must be able to comprehend in order to communicate with one another, regardless of the variations in their infrastructure and designs. Without protocols, devices couldn’t understand the electronic signals they send via network connections to one another. In general, network protocols serve these essential functions:
- Give the information to the right people.
- Receive messages and respond appropriately
- Physically transmit data from source to destination, with security protection.
To get a clear understanding of network protocol, consider comparing network protocols and how a postal service manages actual paper mail. Network protocols maintain continuous data flow through numerous channels, just as the postal service keeps letters from various origins and destinations. However, network protocols offer more sophisticated capabilities than physical mail does. These consist of automatically creating duplicates of a message for delivery to numerous locations at once and streaming a continuous flow of messages to one destination (called broadcasting).
How Does Network Protocols Work?
Like most of the other data networks, the internet divides data into small bits called packets. Every large message transmitted between two network devices is often divided into smaller packets in order to improve the network’s performance and stability. Each packet consists of three primary parts: a header, a payload, and a footer. The network needs context-specific information, such as sending and receiving device addresses, which are found in packet headers and footers.
They also include extra information that makes network connections more reliable and efficient, such as checksums that help network applications detect data corruption or manipulation and counters that keep track of the order in which communications were sent. The data to be transferred is included in the payloads portion.
In general, all network protocol models operate in similar ways. But each protocol is distinct and operates in accordance with the rules laid down by the organization that founded it. Understanding the nuances of network protocols requires a solid understanding of the Open Systems Interconnection (OSI) concept. The OSI model, which is recognized as the basic architectural framework for communications over the internet, is the foundation for the majority of existing network protocols.
The seven layers of the OSI model are used to divide the communication between two network devices. Each of these seven layers is given a set of tasks and each layer is independent of the others, allowing each to independently do its duties. Here is an illustration of the communication process between two network devices using the OSI model to bring this into context.
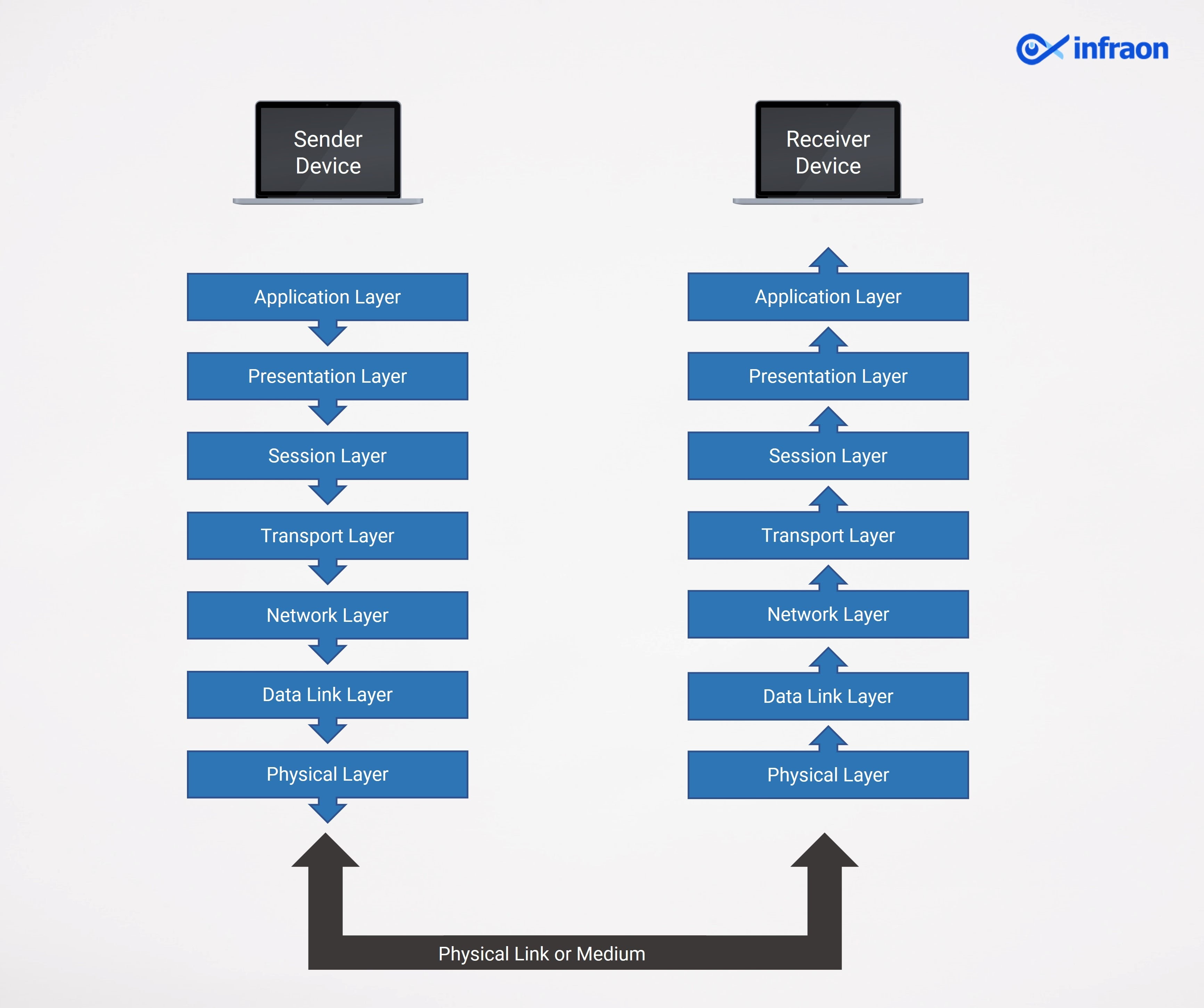
Let’s look at the detailed descriptions of the functioning of network protocols in each layer of the OSI model:
Application Layer
The topmost layer of the OSI model is the application layer. The majority of network applications that use the internet use this layer. It primarily serves as an interface between the user and network services.
Presentation Layer
The presentation layer is primarily used in networks to perform data translation, encryption and decryption, and compression. It is responsible for data transmission between two systems, including syntax and semantics.
Session Layer
The session layer creates connections between the devices to allow for data transmission and reception. It also closes the connections once the data has been transferred. It primarily handles authentication and authorization by creating a secure connection in the network.
Transport Layer
It is mostly in charge of delivering the data from one process to another. It controls the data’s flow and errors to ensure appropriate transmission. The transport layer regulates the communication’s reliability through a variety of features.
Network Layer
The primary function of the network layer is data transmission between computers in various networks. If the data is being transmitted across the same network, this layer might not be as useful. Logical addressing (IP addressing) of the data is done at the network layer.
Data-Link Layer
The data-link layer handles the physical addressing of data. It offers a way for data to be transferred over local media from one computer to another and is embedded as software in the NIC (Network Interface Card).
Physical Layer
The physical layer, which deals with data in the form of bits or signals, is the lowest layer in the OSI model. The physical layer will receive the data from the higher layer at the sender’s end, transform it to bitstreams (0s and 1s), and then deliver it across a physical channel. The bitstreams will be transformed into frames at the receiver’s end and transmitted to the data-link layer.
List of Network Protocols
You may be familiar with some network protocols found in your everyday internet browsing, but there are many other network protocols to choose from. Let’s divide network protocols into three major groupings based on their functions to make things easier. Nearly all network protocols perform the following three fundamental responsibilities:
- Security
- Communication
- Network Management
Security Protocols
Security protocols maintain the confidentiality and integrity of data as it moves through a network connection. These protocols outline the proper ways to protect data from unauthorized efforts to review or extract information. Encryption, entity authentication, and transportation are always included as standard elements in security network protocols.
Some common examples of security protocols include the following protocols:
Secure Sockets Layer Protocol (SSL)
SSL is a standard for internet security that employs encryption to guarantee the confidentiality and integrity of data. The handshake protocol, the record protocol, and the alert protocol are three sub-parts of this layer, which are located between the application and transport layers.
Transport Layer Security Protocol (TLS)
This protocol creates a key using a pseudo-random technique to encrypt data transmission between protocol clients and protocol servers, such as when a web browser requests a webpage from an online server.
Secure HyperText Transfer Protocol (SHTTP)
This protocol includes a variety of security precautions, like setting up a firewall and using strong passwords to secure internet communication. At the application layer, this protocol encrypts and authenticates each message.
Communication Protocols
Communication protocols are formally stated standards and formats for digital messages. These protocols can be used for important operations, including file transfers between devices and internet access, as well as analog and digital conversations. The main purpose of these protocols is to send messages from one computer system to another. They play a crucial role in telecommunications systems since they often send and receive messages.
The following are a few typical examples of communication protocols:
Transmission Control Protocol (TCP)
This is a popular communication protocol that helps in network communication. It divides any message into a series of packets which are then transferred from the source to the destination and assembled there.
Internet Protocol (IP)
This protocol is created specifically to be an addressing protocol. It mostly relates to TCP. The IP addresses in packets help with routing through different network nodes until they reach the target system. The most used network connection protocol is TCP/IP.
User Datagram Protocol (UDP)
UDP is a communication protocol used for time-sensitive transfers, including DNS lookups or video playback. It speeds up communications without explicitly establishing a connection before data is transferred.
Network Management Protocols
The network management protocol is a group of network protocols that specify the steps to manage, monitor and maintain a computer network. These protocols make it simpler to monitor and report data and traffic that is moving to and from a host and a client device.
Some examples of network management protocols include:
Simple Network Management Protocol (SNMP)
The simple network management protocol (SNMP) is a widely used internet standard protocol for managing and keeping track of network devices linked over IP. Using SNMP, devices such as wireless devices, servers, CCTV cameras, routers, switches, firewalls, load balancers, and switches communicate with one another.
Internet Control Message Protocol (ICMP)
Network diagnostics and error reporting are done via the Internet Control Message Protocol (ICMP). When data does not pass through as it should during the error reporting process, ICMP sends messages from the sender to the receiver. Ping and traceroute use ICMP packets sent during the diagnostic procedure to provide information about how data is delivered.
Cisco Discovery Protocol (CDP)
Cisco systems created CDP specifically for sharing information between connected cisco devices with a direct link. It is used to gather data on devices that are directly connected to one another, including hardware, software, device name information, and many other things. Without physically inspecting the equipment, it aids in an effective inspection. A user of CDP can inspect information on connected devices, such as hostname, local and remote ports, and specifics on the connected devices’ platforms, by using a variety of show commands.
Examples of Network Protocols
Here are a few examples of the most commonly used network protocols:
Hypertext Transfer Protocol (HTTP)
The Hypertext Transfer Protocol (HTTP), which is used to load websites with hypertext links, was the foundation on which the World Wide Web was created. HTTP is an application layer protocol that operates on top of other layers of the network protocol stack and is used to transfer data between networked devices. A client computer sends a server an HTTP request, and the server replies with a message.
Secure Socket Shell (SSH)
SSH is a cryptographic protocol that offers secure computer network communication. It is a network protocol that provides users, in particular system administrators, with a safe method of accessing a computer via an unsecured network.
Short Message Service (SMS)
To send and receive text messages over cellular networks, this communication protocol was developed. SMS only relates to text-based communications. Multimedia Messaging Service (MMS), an expansion of the SMS protocol, is required for sending images, movies, or other types of material.
Related Article: Types of Network Performance Monitoring Tools
Final Note
In the modern world, users communicate through a variety of applications, devices, languages, and data transfer methods. If there were no set of rules that could control how people communicate for data and how our devices treat that data, global communication would therefore be impossible. Therefore, as technology advances, there will always be a need for and importance of network protocols. Furthermore, network protocols do not simply define how devices and processes work; they define how they can work together. Without these predetermined standards and rules, the internet would lack the necessary infrastructure it requires to be functional.